
Data Center Security Solution
- Category: Solutions
- Publish Time: 2021-04-13 17:01:24
- Views: 0
Solution Introduction
The rapid development of web services has attracted strong attention from hackers, leading to prominent web security threats. Hackers can easily gain control of web servers by exploiting vulnerabilities in website operating systems and service programs, enabling them to tamper with webpage content, steal important data, inject malicious code, launch denial of service attacks, and carry out various malicious purposes that harm both website operators and visitors. This has led to increasing user concern about application layer security issues and growing attention to website security. Additionally, endpoints infected with viruses and trojans accessing internal services pose security threats to core business operations. Therefore, data center security construction is an essential part of overall network infrastructure development.
Solution Topology
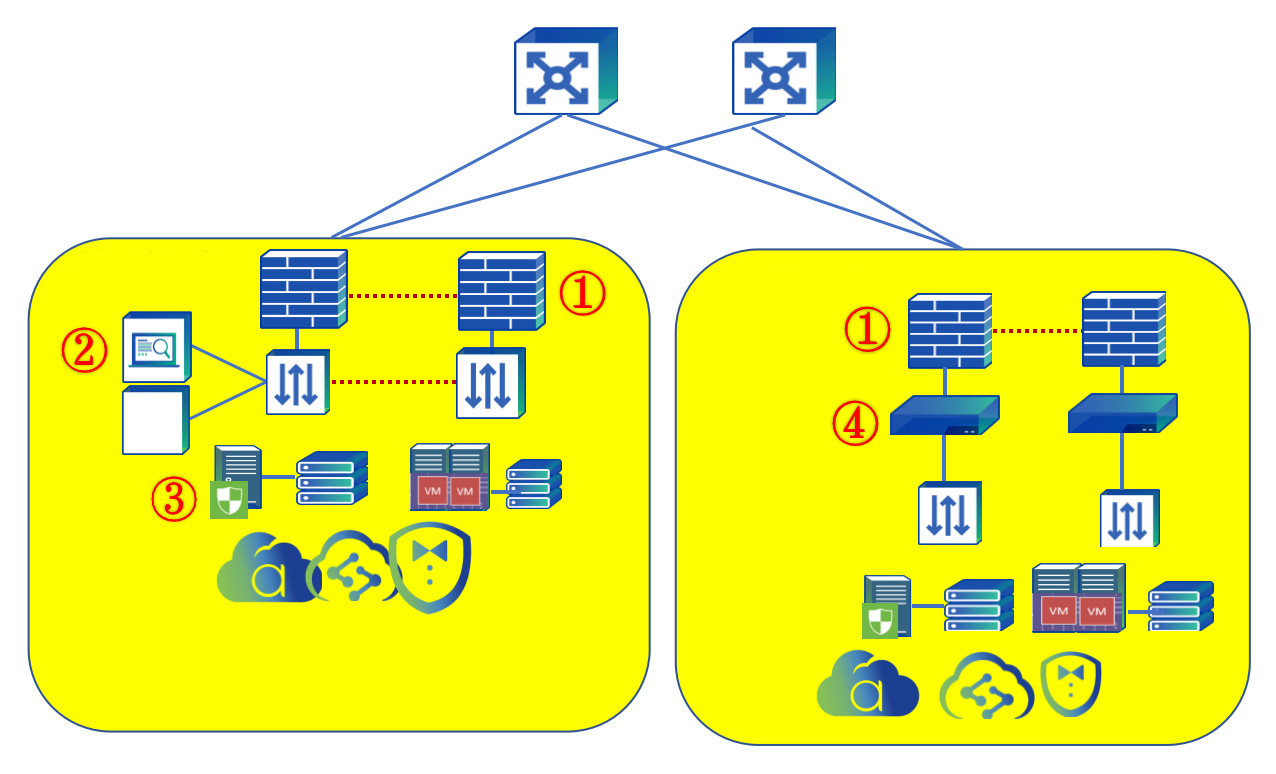
User Benefits
① Integrated Security with Full Visibility: The NGAF defense system, based on security event cycles, analyzes hacker attack motives and timing. It provides unified protection throughout the "before", "during", and "after" stages of hacker attacks, forming effective integrated protection across layers 2-7 based on the security event lifecycle.
② Audit Operations and Source Tracing: Database auditing enables real-time monitoring of all external and internal user database operations and content, with real-time alerts for high-risk operations. All activities can be queried, traced, and analyzed afterward for investigation purposes.
③ Proactive Defense Against Ransomware: With an asset-centric approach, we provide precise and continuous detection capabilities, helping customers quickly resolve issues through coordinated response. ZCZYTECH EDR accurately identifies different ransomware families and detects various ransomware infection behaviors and encryption characteristics through professional analysis, effectively preventing users from being infected by the latest ransomware. ZCZYTECH's EDR actively detects brute force attacks and blocks IPs showing attack behavior. For Web security attacks, it actively detects Web backdoor files. Against botnet attacks, it quickly locates and removes botnet files based on botnet activity patterns. The EDR product can quickly analyze network-wide threats based on IOC intelligence data, promptly discover and respond to the latest security events, and conduct source tracing analysis using historical behavior data to prevent organizations from receiving security incident notifications.
④ Fast and Stable Access for Users: Server load balancing implements intelligent routing for quick access based on corresponding load balancing algorithms. When user requests reach the load balancing device, pre-configured load policies ensure reasonable and rapid distribution of each connection to the most suitable server, improving server utilization and ensuring fast and stable user access.
